Data Governance, Data Security and Privacy
There have been 1,619 publicly reported incidents of cyber-attacks in schools within the US from 2016 to 2022 according to The K – 12 Cybersecurity Resource Center. Because of this, it is important for school districts to have strong plans in place for data governance, data security and data privacy.
Data governance refers to the overall management of data including; availability, usability, integrity, quality and security. Aligning policies, procedures, responsibilities and controls for each step of the data lifecycle ensures that student data is collected and used in ways that protects students and their family’s rights to privacy, security and timely and accurate data.
All school districts should have in place a data governance program that encompasses the following:
- Privacy Policies with adherence to legal and ethical requirements for protecting student data
- Define the data to be protected (PII or sensitive)
- Develop policies for acceptable use of the data
- Identify authorized users of the data
- Procedures to protect data released in public reports
- Process for destroying data no longer needed
- Security policies and procedures focused on technical aspects of protecting data
- Protecting data within technology infrastructure
- Protecting data within user applications and tools
All privacy and security programs should address the phases of the information life cycle.
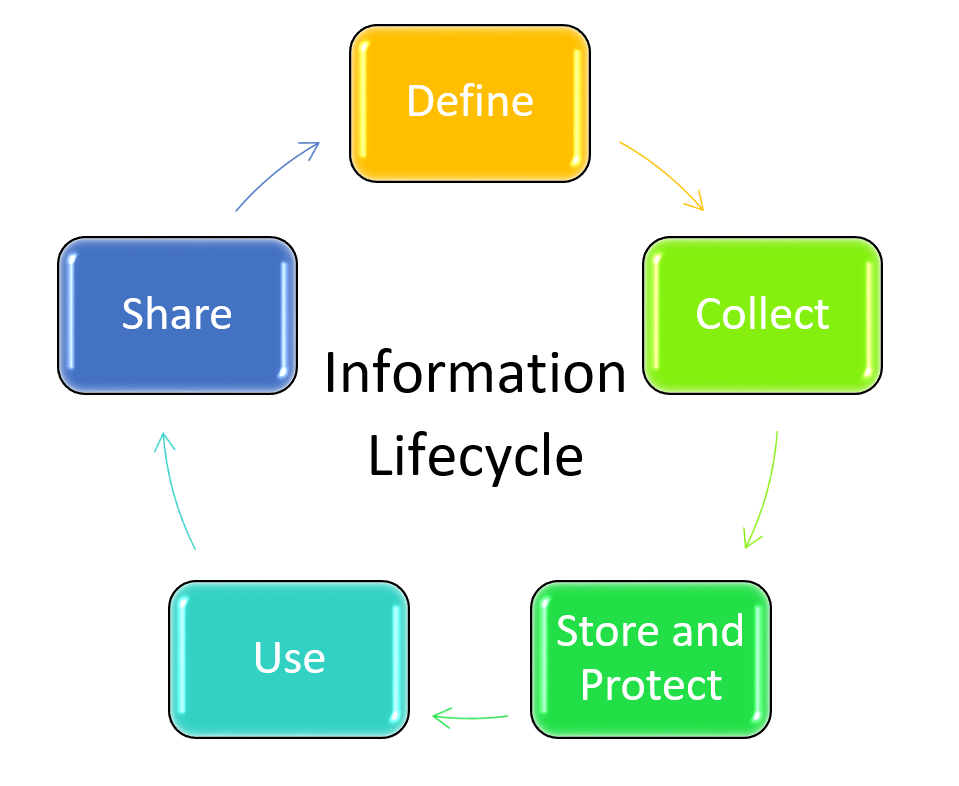
DEFINE – Identify and define data elements needed to comply with reporting requirements, inform decision-making and business processes. Only data needed for a legitimate purpose should be collected.
COLLECT – Some data will only need to be collected once and will remain constant over time. Examples are student name and birth date. Other data will be collected on a recurring basis. Examples are testing data and course enrollments.
STORE AND PROTECT – Some data will be saved in the statewide longitudinal system other data will be saved within the district’s data system or both. No matter where the data is stored the agency housing the data is responsible for the security of that data. Protecting data at any level should include both privacy and security considerations including defining user roles and access rights.
USE – Most important part of the lifecycle. Effective systems facilitate the use of the data to support the district’s work and the students’ educational outcomes. Authorized users will need a variety of tools to access and analyze data.
SHARE – Policies should be in place to guide how, when, under what circumstances and with whom the data will be shared while adhering to privacy laws and regulations.
RETIRE – Timelines for when data should be destroyed or moved into archives for future use (like transcripts).
DATA GOVERNANCE COMMITTEES
At the district level, data governance is typically focused on student K – 12 data. Many districts also share this data among non-profits and other local area community resources, for these districts having a cross-agency data governance structure can be helpful. Whether the data governance is only done within the district or done in a cross-agency structure, a data governance structure should incorporate various levels of responsibility and decision-making. Here is an example is a model for data governance with 4 levels of responsibility.
- Level 1 – A district’s IT department is responsible for the infrastructure and manages the data within the data system. This department also usually manages the technical security of the data.
- Level 2 – Data managers representing a variety of program areas meet regularly and discuss data needs and usage. Ideal participants of this group would represent programs like Assessment, Special Education, Career and Technical Education, Migrant Education and other district chosen programs based on community make-up. In addition, to these participants, several district support staff that maintain or collect student data should be included and can provide greater perspective around the data.
- Level 3 – A lead group of data managers should be appointed to coordinate activities among the data managers, IT staff and other stakeholders. This work should be communicated regularly with district leaders and school building leaders.
- Level 4 – A data policy committee should be put in place to set policies for federal and state legal directives and state and local board policies. A district should consider including local board members and legal counsel or legal advisor, and senior-level administrative staff to this committee. If the district is using the cross-agency structure then community representatives should also be included.
Another way to structure a data governance committee is to identify focus areas of responsibility within a committee. In this model, the data governance committee is responsible for the assignment of roles and responsibilities related to a focus area and ensure all four responsibility levels mentioned above for their focus area.
- Data Inventory – This work entails keeping a complete inventory of all data collected, all data systems for storage and processing data and identifies targeted security and privacy management policies in an effort to protect that student data.
- Data Quality – This work entails providing strategies for preventing, reviewing, detecting and correcting errors within the data system. In addition, they should identify misuse of reported data or apparent breaches of data to unauthorized personnel.
- Data Use and Access – This work entails specifying approved uses of data and identifying authorized users of specific data.
- Data sharing and reporting – this work entails being sure data that is shared complies with federal, state and local laws. Also making sure any data that is shared adheres to policies and regulations, this includes protecting direct and indirect PII in agency shared reports and public reports. This work should also include procedures for regular stakeholder notification about their rights under federal, state and local law.
- Data security and risk management – Creating procedures that will ensure the security of PII and sensitive data by protecting against the risk of unauthorized disclosure should also be a component of the data governance program.
NOTE – Electronic data is often the focus of data governance programs but, paper records must also be protected from misuse and unauthorized access. Paper records can also only be shared according to federal, state and local policies. Paper records should always be stored securely and disposed of properly when no longer needed according to the district’s records retention policy.
DATA SECURITY
Data security is how data are collected stored and transferred through a district’s infrastructure. Infrastructure includes district-owned servers and devices, including mobile devices. All district-controlled applications, networks and cloud-based storage should also be included. Traditionally, firewalls served as the divide between internal and external security threats but now this is not always the case. Increased use of mobile devices both personal and district-owned devices along with the increased usage of online applications in the classroom has brought new challenges and more potential security risks.
There are two main types of risks to be mitigated by school districts. Technical risks like hackers and human risks like passwords written on easily found sticky notes. Having a comprehensive security plan can reduce both types of risk. A district security plan should include two major areas of policies:
- Policies and guidelines for work and personal use of district-owned devices and data systems as well as working from personal devices.
- Policies and guidelines for data use, assessing data risk, how to handle breaches, and how the compliance of these policies is monitored.
Regular professional development and compliance audits are necessary to be sure procedures are understood and followed. Poorly trained staff can result in unnecessary breaches and be costly to a school district. Here are some ways a district can protect itself from technical and human threats:
- Physical security – protect computing resources from unauthorized access by securing areas where PII or sensitive data are stored. Monitor access to these areas by requiring digital ID badges or having visitors log in prior to gaining access.
- Network security – Create a network map that includes servers, routers, applications, and data. The map should show dependencies and highlight vulnerabilities. The use of firewalls and intrusion prevention systems should be put in place. Firewalls and the rules they follow for either permitting or denying network transmissions should be examined. Regular reporting of suspicious or malicious activity should be put into place and monitored.
- Secure configurations – New hardware or software should never be introduced into a network without being tested and configured properly. Incorrect configurations and permissions can unintentionally leave a technical system vulnerable.
- Patch management – Regular use of patches to protect against vulnerabilities is common in the world of technology. Patches should be applied as part of a plan for regular system testing and for rollouts of software updates.
- Two-factor authentication – Identification of authorized users is traditionally done with passwords, key cards, or biometrics (like fingerprints). Two-factor authentication requires the use of two of these methods to gain access.
- Access control – Requiring strong passwords, locking devices that have been idle for a period of time, setting multiple levels of user authentication and limiting access to sensitive data to only those who need to know for the purpose of their work is an important part of security.
- Encryption of data – Data that is stored in servers and mobile devices needs to be encrypted. This will help to control the likelihood that sensitive data could be retrieved from such devices in case they are stolen or lost. In addition, data that is being sent via email should also be encrypted or desensitized before it is sent.
- Staff security training – There are many common issues that can be problematic among staff. Staff negligence can often result in data and security breaches. It is important to have procedures for staff to follow in the event they have caused some exposure. Here is a link to PTAC’s password data breach response training kit and their data breach response checklist to assist districts in the preparation of this training. These resources contain multiple resources for district use.
Topics that should be covered in this training are listed below.
-
- Password Management
- Locking computers
- Sending sensitive data via email
- Using Personal mobile devices
- Data destruction
- Phishing
PRIVACY PROGRAMS
Having a strong district privacy program can demonstrate both compliance with the law and proper ethical use of PII. Having a strong security program in place can go a long way in supporting the implementation of a privacy program. A privacy program is a set of policies and procedures to keep PII safe, comply with laws and policies and protect both students and the district from harm. If you determine a privacy program is needed there are several steps to build this program.
- A privacy coordinator should be appointed. Requirements of this position should include the coordination of privacy efforts and policies.
- The coordinator should work with the data governance council and/or legal staff to determine which privacy procedures and policies are in place.
- The coordinator is responsible for bringing all of the necessary people together to determine needs for each step of the data lifecycle.
- The coordinator should develop and provide all data training to district staff.
- The coordinator should constantly monitor to ensure policies and procedures are being followed.
- The coordinator should assist in creating the messaging to stakeholders about districts’ efforts around student data privacy.
Here is a short 2-minute video from PTAC that gives more information on privacy programs. Video – Developing a Privacy Policy for your District
TRANSPARENCY
Many of the laws require regular notification to the public about student data that is collected by a district. In addition, in some cases, districts must share how they use the data and how they protect confidentiality. Providing transparency around a school district’s plan is not just part of the law but part of good practice.
Here are some suggestions for maximizing transparency with the public:
- Place information about student data policies and practices in an easy to find space on your website
- Provide a detailed data inventory of the student information that is collected and how it is used
- Post vendor contracts online which include the terms of service for online apps and services used in the classroom. For Nebraska school districts using the SDPC website is a good option.
- Share with parents what personal information is shared with third parties and for what purpose(s)
- Publicly provide a staff contact and how they can be reached for stakeholder questions
For more tips on transparency, see PTAC’s Transparency Best Practices for Schools and Districts.
COSTS, BENEFITS AND RISKS
There are costs involved with implementing these data privacy programs including equipment, professional staff, and training of district staff and both time and money can often be in short supply in education. Often these costs can be barriers to districts implementing quality programs until there is a breach or parents raise concerns related to student data privacy. To ease some of the burden, districts can consider the implementation of parts of these programs over time and as resources allow. Districts need to begin by complying with laws and regulations and gradually expand to security, training and updating equipment. Privacy and security programs will protect districts and their students from potential harm such as theft, predatory activities and emotional and social harm. In the long run, districts can be saved potential financial costs from lawsuits, identity theft, and ransom attacks.
STAFF PROFESSIONAL DEVELOPMENT
There are many aspects to staff training that must be put into place to create success around your data privacy programs. In addition, CIPA law requires additional training for staff to teach students many aspects of proper online behavior, social networking interactions and cyberbullying. Districts are responsible for providing proper training to administrators, teachers and other staff, including contracted employees on data use. Many times this training can be tied to other training staff receives when they join the district. An example would be to provide basic training on data privacy while staff undergoes training on the student information system (SIS). Districts must also provide ongoing training on an annual basis to reinforce policies and procedures or even update on changes. Often districts have Acceptable Use Policies that outline acceptable and prohibited activities that staff must sign each year but this cannot be a substitute for ongoing training that should be occurring.
Here are some topics that could be covered in a staff data training program.
- Definitions of “personally identifiable information” and “sensitive data”
- Federal and State Legal laws and requirements, like FERPA and COPPA
- Nebraska Department of Education Rule 6 and its requirements
- Local board policies related to privacy
- Directory information policies
- District procedures on vetting/approval of classroom used applications and websites
- Processes for managing a data request
- Appropriate uses and sharing of student data
- Protecting student privacy while using online educational services
- Methods for protecting PII in and off site
- Data destruction best practices like shredding and deletion of electronic files
Districts most often have provided this type of training in a face-to-face training experience but increasingly this type of training is being moved to asynchronous online formats. The use of this format provides more flexibility and cost-effectiveness. In addition, there are assurances that all staff receives a consistent message around policies and procedures.




