NDE Data Governance
Why is Data Governance Important?
Data governance has now become the center of data quality in many organizations. Over the years, the importance of data governance has significantly increased, primarily because organizations now preemptively align their data governance process to reduce data security risks. As an educational agency, NDE takes key initiatives to maintain data to make informed decisions that best support our students’ privacy and ensures overall safety of the data we are entrusted with.
Strategic Data Governance
The management of data has now become one of the most crucial elements for all organizations, and therefore, data governance plays a crucial role in managing that data. Educational institutions are increasingly targeted by cyberattacks due to the vast amounts of sensitive data they hold, including student records, financial information, and research data. The shift to digital learning platforms and reliance on third-party services have expanded the attack surface, making schools and universities more susceptible to breaches.
Cloud services have now become an integral part of ensuring systematic data governance and educational systems across the US. This cloud services help in appropriately analyze and assess information to mitigate risks to the integrity, confidentiality, and availability of sensitive institutional information and the personally identifiable information (PII) of students, staff, and others.
The use of technology to provide high quality instruction provides vast opportunities for personalized learning. However, with innovation, we need to balance instructional needs with privacy protections. The data governance webpage serves as a resource for how districts can support best practices at the school level to protect the confidentiality of student data. School districts need to consider federal and state laws, state and local school board policies, parental expectations, student instructional needs, and the current available resources when developing privacy guidelines and procedures.
The data governance webpage provides details on the following information:
- Federal & State Privacy Laws – the legal requirements that must be considered when developing privacy programs
- Data Governance – details the interrelationships of data governance, security, and privacy programs
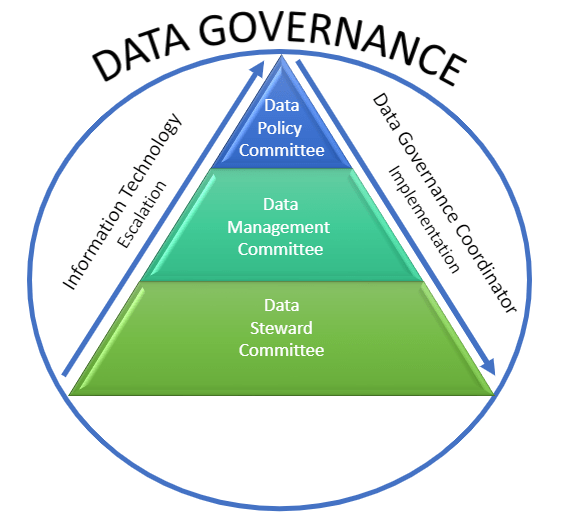
- Data Governance Committees – (Data Management, Data Policy, and Data Steward) are empowered to oversee data-related practices to ensure data is accurate, secure, accessible and used effectively for decision making.
- District Roles and Responsibilities – outlining the roles and responsibilities of different entities in safeguarding student data confidentiality and managing access to protected data.
- Student Data Professional Development programs should be considered for effective staff professional development
- It is important for districts to know they are responsible for establishing and supporting effective data governance, data privacy, and data security programs in addition to compliance with laws and regulations. Providing these programs can also better facilitate effective and innovative instructional practices which are necessary in today’s school environments.
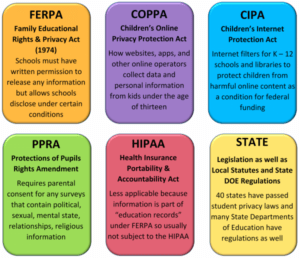 FERPA At a Glance
FERPA At a Glance
- Originally passed in 1974 and has been amended several times
- All schools that receive federal funds are subject to the requirements of FERPA
- The Privacy Technical Assistance Center (PTAC) was established by the U.S. DOE to provide resources
- Provides opportunity for parents and students 18 and over to review student education records
- Prohibits schools from disclosing personally identifiable information (PII) from a student’s records
- Requires districts to notify students and parents each of their FERPA rights
Personally Identifiable information (PII) for FERPA includes but is not limited to:
| Name of a student or their family members | Place of Birth |
| Address or Geolocation information of a student or their family members | Mothers maiden name |
| Social Security numbers | Other online contact information like screen names |
| Student ID numbers | Telephone numbers |
| Email Address | Student’s Date of Birth |
Common exceptions to FERPA
There are allowable exceptions (shown below) which allow districts to use reasonable methods to ensure that any third party that receives student information uses the data for district authorized purposes only. It also requires that the third party destroy all of the data once the data is no longer needed for the purpose which it was shared. Districts should be sure to put these agreements in place before they begin the sharing of student data.
- School official exception – allows districts to share PII to designated school officials with legitimate interest
- Studied exception – allows disclosure of PII to third parties that conducting studies on behalf of educational agencies or institutions
- Audit or evaluation exception – allows disclosure of PII to authorized representatives of federal, state and local education authorities for audit of support educational programs
- Directory information exception – allows certain PII to be disclosed without parent or eligible student (18 and over) consent if they have notified parents what information is designated as directory information
- For more detailed information about FERPA exceptions see the FERPA Exceptions Summary at the PTAC website or click the link below to download the PDF:
PTAC FERPA Exception Summary COPPA At a Glance
- COPPA is administered and enforced by the Federal Trade Commission (FTC).
- The law protects children under the of 13 who use websites, online games and mobile applications
- The vendor is responsible for following the law but, districts have an obligation to oversee the vendors use
- Districts need to be sure an agreement is in place with third party vendors on the use of the data
Personally Identifiable information (PII) for COPPA includes but is not limited to:
| First and last name | Social security number |
| Physical address, including street name and city | Persistent identifier used to recognize a user over time. |
| Online contact information | Photographs, video or audio files |
| Screen name or user names | Geolocation information |
| Telephone numbers | Parent information collected from student online |
CIPA At a Glance
- Enacted by Congress in 2000
- Tied to E-rate funding for school and libraries
- Schools and libraries must have an Internet safety policy that includes protective measures like filters
- Must block pictures that are obscene, considered child pornography or harmful to minors
- Provide education to minors on proper online behavior, social networking interactions and cyberbullying
More information about CIPA can be found on the FCC website or this FCC website on CIPA . PPRA At a Glance
- Regulates collecting student’s personal information on certain sensitive topics (see details below)
- Parents must be able to see any instructional or survey material used with their children
- Parents have the right to withhold their child from participating
Generally, there are 8 protected areas:
| Political affiliation or beliefs of student or parents | Critical appraisals of people student has family relationships with |
| Mental or psychological problems | Legally recognized relationships, like attorneys, doctors and ministers |
| Sex behaviors and attitudes | Religious practices, affiliations or beliefs of student or parents |
| Illegal, anti-social, self-incriminating or demeaning behavior | Income (other than required by law for eligibility of program or financial assistance) |
More details can be found on PPRA at the following external website: https://studentprivacy.ed.gov/ HIPAA At a Glance
- Enacted in 1996
- Protects the confidentiality and security of healthcare information
- HIPAA rarely applies to K – 12 schools because most school collected records are considered education records bound by FERPA instead
- More guidance on HIPAA as it relates to FERPA can be found on the Student Privacy website on FERPA guidance.
State Guidance at a Glance
- NE state statutes related to Student Data Privacy are:
- Board policy for these statutes is summarized in Rules
Data Governance at Nebraska Department of Education
 At NDE, the key focus is on taking decisions through an informed and verified manner by effectively using data resources.
At NDE, the key focus is on taking decisions through an informed and verified manner by effectively using data resources.
- Data governance brings more insight into matters such as decision making, issue resolution, and collaboratively managing committees like Data Management and Data Stewards Committees.
- Helps in working target focused when budgets are tight with maximum use of resources.
- Given regulations around FERPA, PII, and PTAC, the NDE needs to know where data is at—who is accessing it, where it’s stored, where it’s going, and how it will ultimately be used.
- Data collected from 245 Public School Districts – 1229 Schools (71 PK, 688 elementary,155 Middle/Jr. high, 173 Secondary Schools, & 142 High Schools) is maintained and used as per the needs in compliance with various regulations.
Best Practices in Working with Data
The main objective of data storage is to keep it safe. To ensure the safety of data, it must be kept in a protected environment, with different accessibility levels as per the requirements. Further ensuring data is encrypted, never saved on personal machines or stored on unauthorized electronics devices like pen drives, hard drives, etc.
Note: We can add link to policies after, we have approved policies
Limiting Access Control
Allowing external vendors and contractors to access data is common. Proper controls ensure safe, productive collaboration by limiting access to essential info and safeguarding sensitive data. For best practices in secure vendor access, continue reading.
Sending & Sharing Data
Sending and sharing data immediately without ensuring security can quickly put you at risk. Below is mentioned some of the best practices that can help minimize security issues:
- Avoid emailing data.
- Never save data on an unencrypted machine or an unencrypted USB—always save on a server.
- Any publicly shared information should not identify individual students, critical to abide with PII.
- Date your files and always share the most recent and up-to-date version.
- Limit your recipients. Data leaks and security breaches often start internally. Limiting file access to a ‘need to know’ basis mitigates risk and ensures that confidential documents are only viewed by a select group.
- Think before you send. Before sharing data, consider your rationale. Do you need help with problem-solving? Will another set of eyes make the result better? If you can’t come up with a concrete reason why someone else needs to see the data, it’s better left unshared.
- The data is not your own- it is NDE’s asset. If you need to submit any data outside the organization, please submit a request to the appropriate team to send it out securely.




